Automated bioprocessing systems are critical for cultivated meat production but are vulnerable to cyberattacks. Threats like sabotage, data theft, and ransomware can disrupt operations, damage equipment, or compromise product quality. To protect these systems, a layered security approach is essential, combining physical, software, and network measures to safeguard critical processes and intellectual property.
Key Highlights:
- Risks: Cyberattacks can manipulate bioprocess parameters, leading to quality issues or production delays.
- Physical Security: Use biometric access, RFID badges, and AI surveillance to control equipment access.
- System Security: Validate systems, enable audit trails, and ensure data integrity.
- Network Security: Implement multifactor authentication, segment networks, and encrypt data.
- Continuous Monitoring: Use real-time alerts and conduct regular cybersecurity audits.
These measures help cultivate a secure environment for bioprocessing automation, reducing vulnerabilities and ensuring operational reliability.
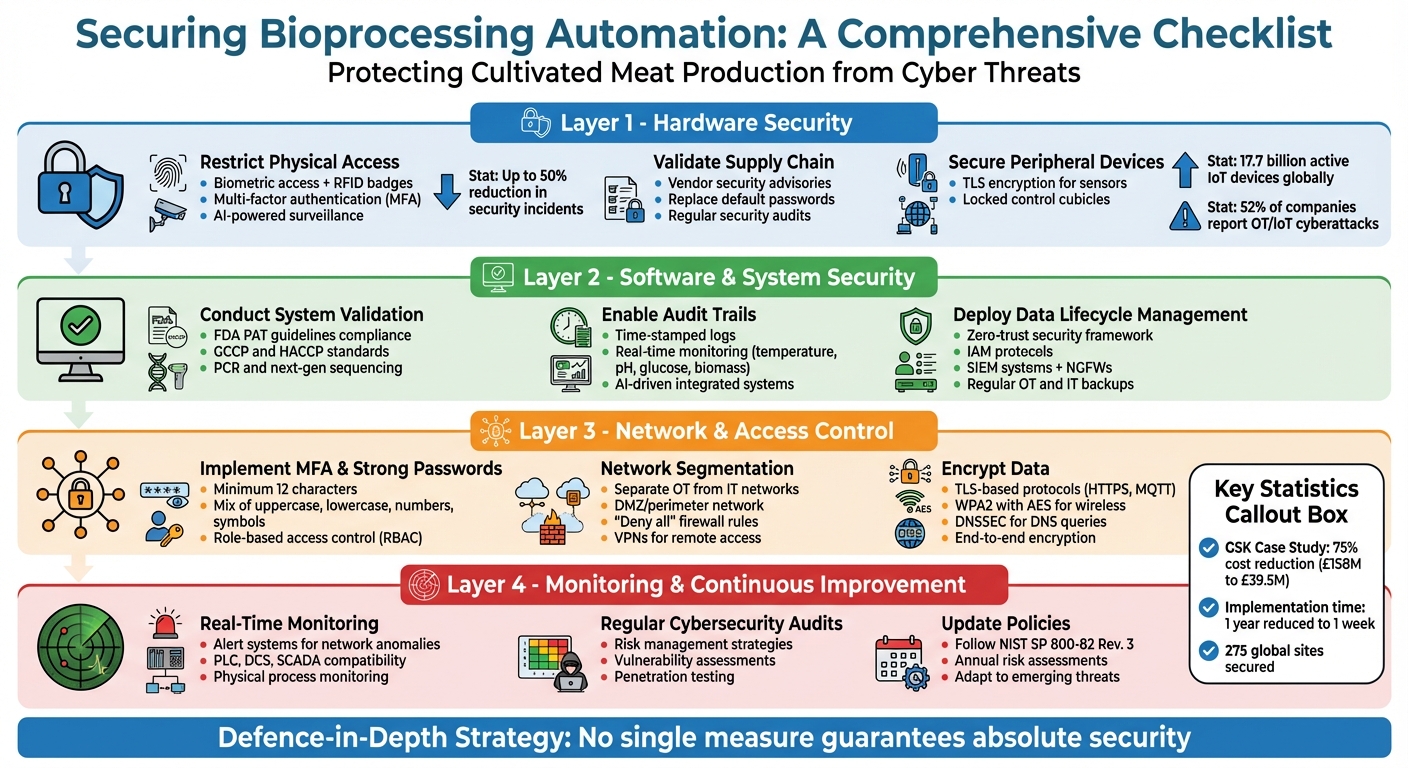
Four-Layer Security Checklist for Bioprocessing Automation Systems
Hardware Security Checklist
Restrict Physical Access to Equipment
Protecting bioprocessing equipment begins with strong physical access controls. Combining tools like biometrics, RFID badges, and smart cards creates multiple layers of security to prevent unauthorised entry [1][2]. Adding multi-factor authentication (MFA) strengthens this further - requiring both a physical badge and a PIN or mobile credential helps block the use of cloned or shared cards.
Data highlights that poor visitor controls often lead to breaches, while biometric and RFID systems can reduce incidents by up to 50% [1]. Visitor Management Systems should include features like pre-registration, photo ID verification, and real-time tracking of guests. Additionally, AI-powered surveillance can spot unusual activities, such as loitering near sensitive equipment or tailgating through secure doors, and alert security teams instantly [1][2].
A notable example comes from GSK, which in 2025 introduced identity-based microsegmentation across 275 global sites under the direction of CISO Michael Elmore. This initiative reduced the time to secure a site from a year to just a week, cutting costs from an estimated £158 million to £39.5 million - a remarkable 75% reduction [3]. Reflecting on the stakes, Elmore stated:
Coming to Pharma and recognising that we're putting things in people's body scared me straight as a CISO. Whether that's vaccine, HIV medication, the safety impacts that come with not getting this right viscerally keeps me up at night [3].
Validate Supply Chain Integrity
Physical security is just one piece of the puzzle - securing the supply chain is equally critical. Implement strict security policies for all hardware, solutions, and service providers to ensure consistent standards [4]. Vendor security advisories, like Siemens ProductCERT, can help track and address vulnerabilities in industrial products [4]. For single-use systems, confirm that components such as bioreactor bags comply with stringent regulatory standards. This not only ensures safety but also prevents costly losses of high-value batches [5].
During commissioning, replace default passwords immediately and deactivate unused interfaces like USB, Ethernet/PROFINET, and Bluetooth [4]. Introduce thorough testing for external data carriers and peripherals before they enter production areas. Regular security audits are essential to verify that these measures effectively mitigate risks [4].
Cultivated meat companies can also enhance supply chain security by sourcing hardware from verified suppliers through trusted B2B platforms like Cellbase.
Secure Peripheral Devices
Once hardware is secured, attention should turn to connected devices. Modern Ethernet or Wi-Fi sensors must include TLS encryption, anti-replay signed messages, and secure authentication protocols [6][7]. Critical automation components should be stored in locked control cubicles or rooms equipped with surveillance systems and alarms [4]. With 17.7 billion active IoT devices globally and 52% of companies reporting OT or IoT cyberattacks, robust measures are non-negotiable [7].
In mid-2025, Andelyn Biosciences implemented identity-based security for its advanced gene therapy manufacturing facility. Led by VP of Information Technology Bryan Holmes, the system provided detailed visibility and enforced strict policies to prevent unauthorised movement between manufacturing zones. This approach ensured that cybersecurity threats would not compromise patient safety or delay product release, even for treatments requiring six-week production cycles [3].
For added protection, use tamper-detection sensors to monitor if devices are opened or cables are disconnected - especially in remote locations [6][8]. Disable unnecessary services, such as embedded web servers or FTP, unless they are essential for operation. Establish a routine for evaluating and applying firmware updates to sensors and PLCs, ensuring they remain secure and functional [4].
Software and System Security Checklist
Conduct System Validation
To ensure compliance with FDA PAT guidelines, GCCP, and HACCP, it's essential to monitor key parameters in real time [5][10][12]. Incorporating PCR and next-generation sequencing into validation protocols can confirm the absence of contamination in cell cultures [11]. Additionally, in-line sensors used in automation should be validated to function reliably for weeks without needing re-calibration and must withstand sterilisation processes without releasing unwanted components [5].
Using automated, closed-system biopsies and bioreactors minimises human error and contamination risks, which are critical for meeting regulatory safety standards [11]. For cultivated meat companies, sourcing pre-validated equipment from platforms like Cellbase can simplify compliance with these strict requirements.
After completing system validation, the focus should shift to implementing comprehensive audit trails and ensuring data integrity to maintain consistent performance.
Enable Audit Trails and Data Integrity
Establish time-stamped audit trails, integrate PAT-driven real-time monitoring, and deploy sensor arrays to track critical variables, ensuring the integrity of collected data [5][13]. Automated sampling systems can deliver precise, frequent data on key factors like metabolites and nutrient levels, reducing the risks of manual intervention and potential contamination [13].
Real-time monitoring tools should continuously track essential variables, including temperature, oxygen, carbon dioxide, pH levels, glucose, biomass, and metabolites [5]. Transitioning from manual and disjointed processes to integrated, AI-driven systems helps ensure consistent workflows and predictable outcomes [13].
Once validation and audit trails are in place, it's crucial to secure data throughout its lifecycle to protect against potential threats.
Deploy Data Lifecycle Management
Implement a zero-trust security framework with strict Identity and Access Management (IAM) protocols and least-privilege access controls [14]. Educate employees on proper credential management and promptly revoke access for former employees or temporary users to maintain security.
Use Security Information and Event Management (SIEM) systems and Next-Generation Firewalls (NGFWs) to monitor data packets for suspicious activity and malware. As highlighted by Fortinet:
To both recover and plan for a more secure system in the future, you need a forensics system that is tamper-proof. This may require the implementation of an immutable security log system [14].
Ensure regular backups of both OT and IT systems to allow recovery to a secure state in case of compromise or failure [9]. Additionally, leverage CISA's Cyber Vulnerability and Web Applications Scanning programmes to identify and mitigate potential threats in automated systems. Prioritise patching vulnerabilities listed in CISA's Known Exploited Vulnerabilities catalogue to further strengthen system defences [9].
Network and Access Control Checklist
Implement Multifactor Authentication and Strong Passwords
Multifactor authentication (MFA) adds an extra layer of protection by requiring at least two separate methods of verification, such as a password combined with a mobile app code or a biometric scan, to secure access points [15][16]. Dr Ir Charles Lim, Head of Cybersecurity Research Centre of Excellence at Swiss German University, highlights its importance:
MFA adds a crucial extra layer of security, requiring multiple verification methods (e.g., password, code from a mobile app, biometric scan) for access to critical systems [15].
This approach is particularly vital for securing remote entry points like VPNs and remote desktop portals, which are common targets for credential-based attacks [15][16].
To enhance security further, pair MFA with role-based access control (RBAC). This ensures that individuals, such as clinical teams or developers, can only access the systems or data necessary for their specific roles [16]. Additionally, enforce strong password policies by requiring passwords to be at least 12 characters long and include a mix of uppercase and lowercase letters, numbers, and symbols [15][4]. When acquiring new bioprocessing automation equipment, prioritise vendors that offer "Secure by Demand" products with robust authentication and secure default settings [17]. For cultivated meat companies, platforms like Cellbase connect procurement specialists with verified suppliers that provide secure bioprocessing equipment.
Once access controls are in place, the next step is to organise your network for better protection of critical systems.
Network Segmentation and VPN Usage
Network segmentation is a key measure to complement your existing security setup. To safeguard critical systems, separate production (OT) networks from corporate (IT) networks [4]. Siemens operational guidelines provide a clear example:
Direct communication between the production and the company networks is completely blocked by firewalls; communication can take place only indirectly via servers in the DMZ network [4].
A demilitarised zone (DMZ) or perimeter network ensures any communication between these networks happens securely via dedicated servers. Within the production network, group components into secured cells based on their protection needs and enforce the "need-to-connect" principle [4].
Firewalls should be configured with a "deny all" rule as the default, only allowing access to the minimum resources required. This approach supports the principle of least privilege [18]. To further enhance security, apply bandwidth restrictions at cell firewalls or switches to prevent external network overloads from disrupting data transfer within critical cells [4]. Disabling unused network interfaces on critical systems is another effective way to reduce risks. For remote maintenance and inter-cell communication, use Virtual Private Networks (VPNs) to establish secure, encrypted tunnels over untrusted networks [18][4].
Encrypt Data at Rest and in Transit
Encryption is essential for protecting information both during transfer and while stored. Use TLS-based protocols like HTTPS or MQTT over TLS, assigning individual certificates to PLCs to ensure secure and authenticated communication [4]. Siemens operational guidelines recommend:
Only TLS-based communication protocols, such as HTTPS or MQTT over TLS, are recommended for device access and data transfer [4].
For wireless connections, employ WPA2 with Advanced Encryption Standard (AES) to secure WLAN data [4]. Protect DNS queries within your network by implementing DNS Security Extensions (DNSSEC) [18].
To safeguard data at rest, store sensitive industrial project files in encrypted drive containers to protect intellectual property [4]. When transmitting these files, always use encrypted channels. Remote management tools should also operate within a secured, encrypted framework and align with your overall security strategy. For remote access solutions, prioritise those that provide end-to-end encryption and integrate customer-owned identity providers for maximum data protection [4].
sbb-itb-ffee270
Monitoring and Continuous Improvement Checklist
Deploy Real-Time Monitoring and Alerts
Operational Technology (OT) systems in bioprocessing require robust monitoring tools to maintain performance, reliability, safety, and data security while managing critical physical processes like temperature control and bioreactor conditions.
Set up alerts to flag network anomalies and unexpected changes in physical measurements or process events. For instance, an unauthorised change to a Programmable Logic Controller (PLC) could jeopardise an entire batch of cultivated meat. The NIST Guide to Operational Technology Security (SP 800-82r3) highlights the importance of this distinction:
OT encompasses a broad range of programmable systems and devices that interact with the physical environment... These systems and devices detect or cause a direct change through the monitoring and/or control of devices, processes, and events
Design an alert system that prioritises threats affecting physical safety and process integrity over routine IT-related notifications. Ensure the monitoring tools you use are compatible with industrial hardware like PLCs, Distributed Control Systems (DCS), and Supervisory Control and Data Acquisition (SCADA) systems. This compatibility is critical to avoid disruptions in sensitive bioprocessing workflows. These real-time monitoring measures create a solid foundation for regular system audits to verify resilience.
Conduct Regular Cybersecurity Audits
Real-time monitoring is just the first step; regular cybersecurity audits are essential for uncovering vulnerabilities before they can be exploited. In bioprocessing environments, audits should focus on the unique configurations of control systems, including SCADA, DCS, and PLCs. Key areas to examine include risk management strategies, threat detection processes, vulnerability assessments, and the security of networks and sensors.
Customise your audits to the specific needs of OT systems, rather than relying solely on IT-focused scans. Include aspects such as physical access controls and environmental monitoring systems in your review. Penetration testing can also be a valuable tool, simulating real-world attack scenarios to evaluate system defences. When purchasing new bioprocessing equipment, consider platforms like Cellbase to connect with verified suppliers offering systems equipped with built-in security audit features.
Update Policies for Emerging Threats
Cybersecurity threats evolve constantly, and your policies must adapt to keep up. On 28th September 2023, NIST released SP 800-82 Rev. 3, replacing the 2015 version and shifting the focus from traditional Industrial Control Systems (ICS) to a broader OT framework. This change reflects the growing role of networked devices, IoT sensors, and cyber-physical systems in modern bioprocessing, all of which demand integrated security measures.
Regularly review your system topologies to identify new vulnerabilities introduced by peripheral devices or IoT integrations. Ensure that updates to your policies do not compromise real-time performance or safety. Stay informed about updates to national security guidelines - NIST, for example, has flagged potential updates to SP 800-82 for July 2024 to address emerging vulnerabilities. Conduct risk assessments tailored to your system's topology at least once a year, and increase the frequency whenever new automation equipment or connectivity changes are introduced.
Beyond Bioprocessing 4.0 - the Convergence of IT, OT, and Processing Technologies
Conclusion
Safeguarding bioprocessing automation calls for a layered Defence-in-Depth strategy. As Siemens highlights:
Neither a single measure nor a combination of measures can guarantee absolute security [4].
This is particularly relevant for cultivated meat production, where systems often contain valuable intellectual property, making them attractive targets for industrial espionage or sabotage [4][19].
The integration of IT and OT systems has significantly broadened the potential vulnerabilities in modern bioprocessing facilities. What were once isolated production setups now rely on interconnected devices, cloud platforms, and real-time data sharing [19]. Addressing this expanded attack surface requires a coordinated effort across three key areas: Plant Security (such as physical access controls), Network Security (including segmentation and firewalls), and System Integrity (like patch management and system hardening) [4].
However, effective protection isn't just about technology. Siemens reminds us that industrial security is an ongoing process requiring collaboration among plant operators, system integrators, and equipment manufacturers [4].
To ensure comprehensive coverage, a checklist approach can unify the security measures discussed. This might include disabling unused USB ports, implementing application whitelisting, adopting Zero Trust architecture, and conducting annual risk assessments. When purchasing new automation systems, consider using platforms like Cellbase to find verified suppliers who prioritise secure system design.
Cybersecurity is not a one-and-done task. Regular risk analyses - at least once a year or after any facility expansion - are essential. Staying informed about emerging threats through resources like NIST SP 800-82 Rev. 3 can help you adapt to new challenges. Revisiting and updating your security measures ensures your systems stay resilient and capable of withstanding evolving cyber risks. By treating security as an ongoing priority, you can better protect your bioprocessing operations from future threats.
FAQs
What impact can cyberattacks have on automated bioprocessing in cultivated meat production?
Cyberattacks targeting automated bioprocessing systems can cause major disruptions in the production of cultivated meat. These attacks might interfere with control systems, leading to delays, compromised product quality, or even complete operational shutdowns. Beyond operational setbacks, there’s also the risk of sensitive data being stolen - like proprietary recipes or detailed process information - which could jeopardise intellectual property.
In more severe cases, cyberattacks could pose safety risks. For instance, tampering with critical equipment or processes might endanger both the workforce and the production environment. To safeguard operations and ensure the integrity of cultivated meat production, implementing strong cybersecurity measures is not just advisable - it’s essential.
What are the key elements of a robust security strategy for automated bioprocessing systems?
A robust security plan for automated bioprocessing systems hinges on a layered defence strategy, tackling risks at the physical, network, and application levels. Begin with physical security by limiting access to equipment like bioreactors and employing tamper-evident protections. On the network side, adopt network segmentation to keep operational technology (OT) systems separate from IT networks, ensuring that only authorised devices can interact with critical components. Strengthen this by enforcing identity and access management, using role-based permissions and multi-factor authentication to control access within each network zone.
System hardening is another key step - disable any unnecessary services, apply secure configurations, and limit functionality to reduce potential vulnerabilities. Protect data integrity with secure communications, such as encrypted connections (e.g., TLS) and signed firmware updates. To stay ahead of threats, implement continuous monitoring through logging, anomaly detection, and regular security assessments. Additionally, maintain incident-response plans, stick to a regular patching schedule, and ensure backups are verified and ready for quick recovery in case of breaches.
For cultivated meat production lines, this approach might involve securing bioreactor control cabinets, isolating PLCs and sensors on dedicated VLANs, and requiring strong, unique passwords for all devices. Choosing equipment from providers like Cellbase can also help, as their tools come pre-vetted with features like firmware signing and supply-chain traceability, adding an extra layer of security and improving operational reliability.
Why are regular cybersecurity audits crucial for bioprocessing facilities?
Regular cybersecurity audits play a key role in spotting and fixing weaknesses that could expose organisations to data breaches, operational hiccups, or even deliberate attacks. These checks are essential for shielding intellectual property, maintaining the reliability of automated systems, and keeping sensitive data safe from tampering.
They also ensure compliance with strict regulatory requirements, which is crucial for upholding trust and steering clear of costly legal or financial consequences. Staying ahead of cybersecurity risks not only helps operations run more smoothly but also creates a safer space for progress and new ideas.











